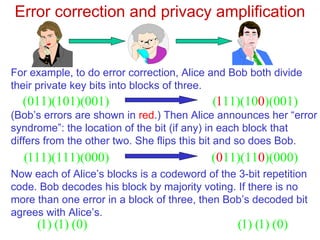
The process of length-compatible privacy amplification algorithm. The... | Download Scientific Diagram
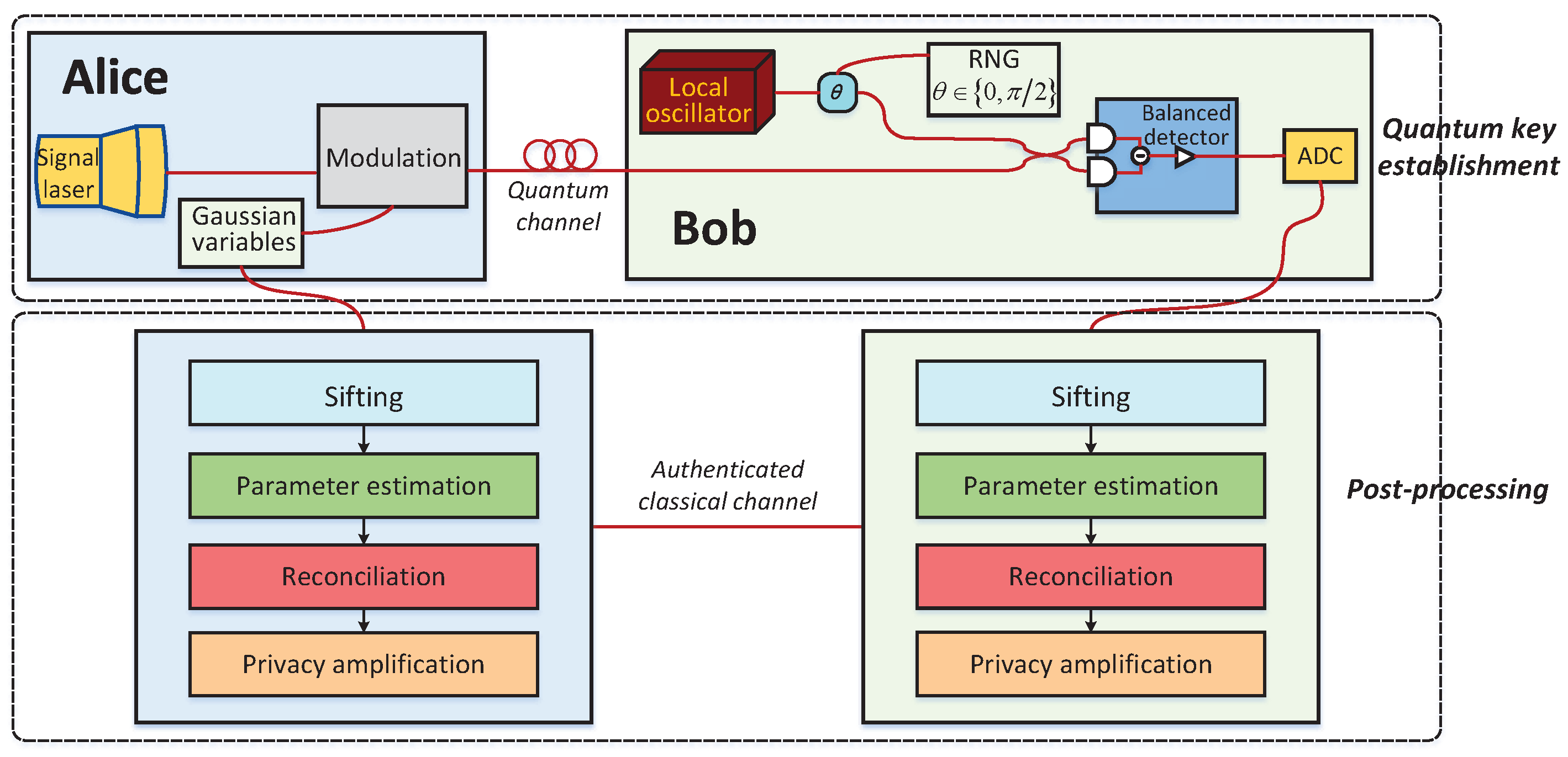
Entropy | Free Full-Text | An Improved Slice Reconciliation Protocol for Continuous-Variable Quantum Key Distribution

PDF) QKD secrecy for privacy amplification matrices with selective individual attacks | Nicola Laurenti - Academia.edu

Analysis of the information theoretically secret key agreement by public discussion - Wang - 2015 - Security and Communication Networks - Wiley Online Library

PPT - Randomness Extraction and Privacy Amplification with quantum eavesdroppers PowerPoint Presentation - ID:4846836
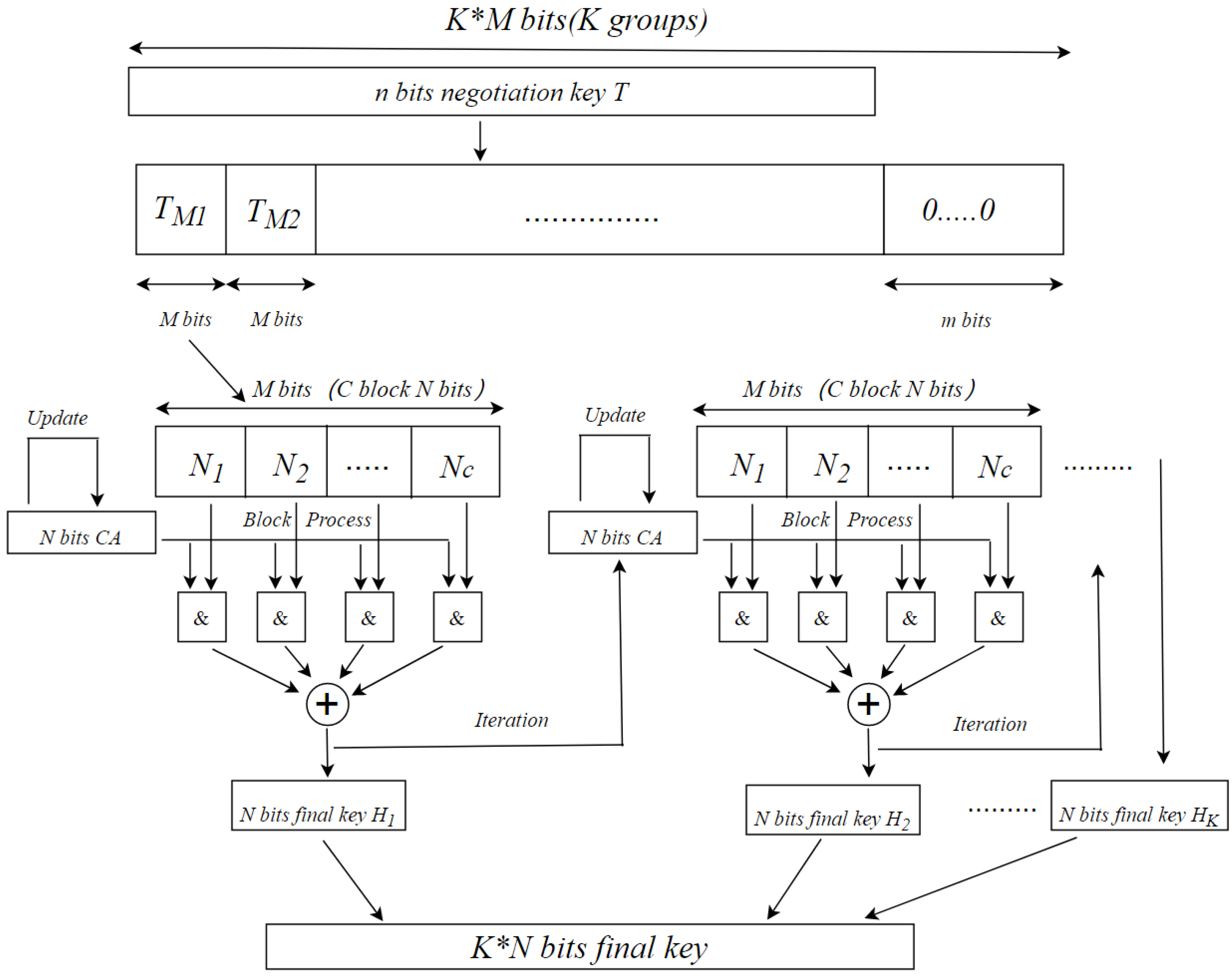
Electronics | Free Full-Text | High-Speed Privacy Amplification Algorithm Using Cellular Automate in Quantum Key Distribution

High-speed and Large-scale Privacy Amplification Scheme for Quantum Key Distribution | Scientific Reports
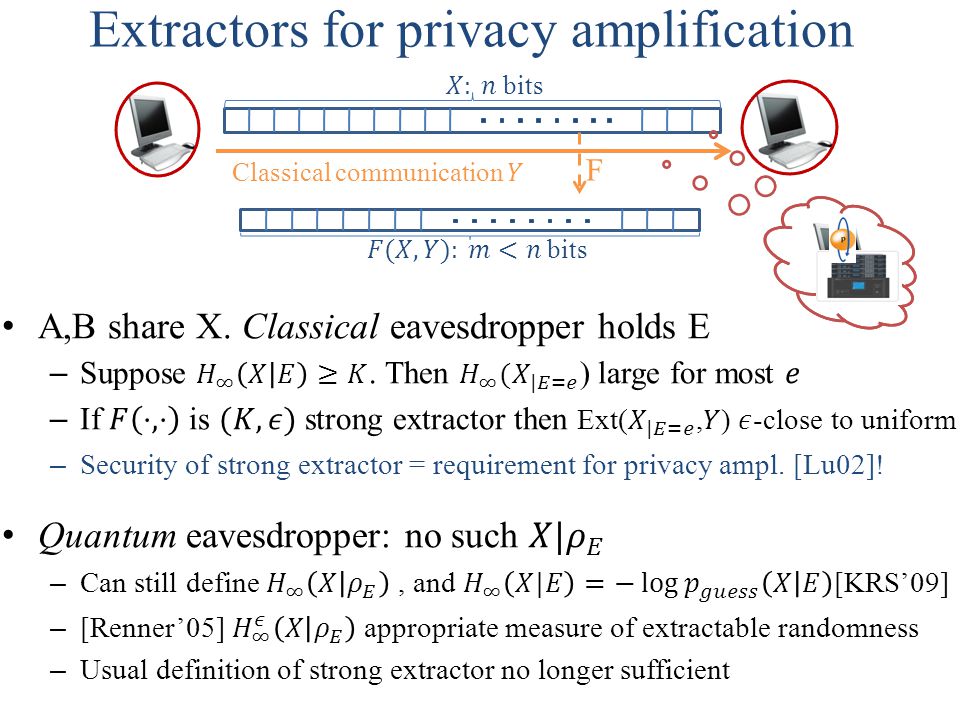
Randomness Extraction and Privacy Amplification with quantum eavesdroppers Thomas Vidick UC Berkeley Based on joint work with Christopher Portmann, Anindya. - ppt download
![PDF] High-Speed Privacy Amplification Scheme Using GMP in Quantum Key Distribution | Semantic Scholar PDF] High-Speed Privacy Amplification Scheme Using GMP in Quantum Key Distribution | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5ab3cb538f80f4bbf539103464fe597ba2d93a7c/1-Figure1-1.png)
PDF] High-Speed Privacy Amplification Scheme Using GMP in Quantum Key Distribution | Semantic Scholar

Quantum Hash function and its application to privacy amplification in quantum key distribution, pseudo-random number generation and image encryption – topic of research paper in Computer and information sciences. Download scholarly article
![PDF] High-Speed and Adaptive FPGA-Based Privacy Amplification in Quantum Key Distribution | Semantic Scholar PDF] High-Speed and Adaptive FPGA-Based Privacy Amplification in Quantum Key Distribution | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/2a6df792aeac6ed6d0db5e99a269b7a34746fa7b/2-Figure1-1.png)

![PDF] Privacy Amplification via Random Check-Ins | Semantic Scholar PDF] Privacy Amplification via Random Check-Ins | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a86aa46da4bcf1daef2e88b7656b7c8477db8e0f/2-Figure1-1.png)